
Cybersecurity is More Important Now Than Ever
Cybersecurity continues to be a crucial concern for individuals, businesses, and governments worldwide, in proportion to its ever-growing utility. Literally a sheath for this double-edged sword, the importance of cybersecurity has grown significantly due to increasing reliance on digital technology across all aspects of life, making it vital to secure computer systems and networks. As digital technology becomes more prevalent across personal and professional contexts, prioritizing protecting digital assets from malicious attacks such as hacking, cyberterrorism, and ransomware is essential. Cybersecurity’s key objective is to protect a wide range of data including personal and financial information, intellectual property, computer networks, and systems. Critical infrastructure such as power grids, banks, and governmental facilities can also be victim to cyberattacks, potentially causing significant disruptions to essential services and posing a threat to public safety and ultimately national security.
Achieving greater cybersecurity requires interdisciplinary inputs from computer science, information technology, engineering, behavioral psychology, data forensics, and law enforcement. Thus, cybersecurity is a multifaceted field that incorporates knowledge and expertise across different areas with one primary goal: to safeguard digital assets from a variety of threats including, but not limited to, identity theft and financial fraud.
Ransomware attacks are among the most audacious and wide-spreading threats faced by local governments; hackers gain access to the public entity’s computer systems and hold them for ransom. Phishing, when attackers use social engineering tactics to trick employees into clicking on malicious links or downloading malware, is another significant threat. Local governments may also encounter distributed denial of service (DDoS) attacks, where hackers flood their systems with traffic, causing them to crash.
Considering the adverse effects of successful cyberattacks, it is crucial to implement cybersecurity measures designed to minimize risk and reduce impact in the event that an attack occurs.
Threats
Cybersecurity threats involve intentional acts by malicious individuals aimed at stealing data, causing harm, or disrupting computer systems which can lead to financial loss, reputational damage, legal penalties, and other negative consequences for individuals or organizations. These threats can originate from diverse sources including hostile nation-states, terrorist organizations, individual hackers, and even insiders such as employees or contractors who abuse their access privileges to perpetrate harmful activities.
Recovery Costs More Than Ransom
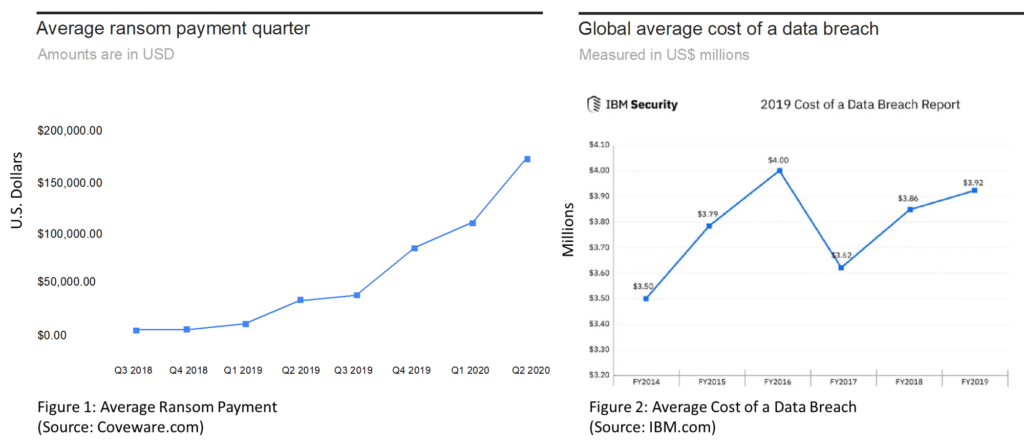
Three common widespread cyberthreats include:
- Malware – A term used for software created to cause damage to computer systems, networks, or devices. This software comes in different forms including viruses, worms, trojans, spyware, ransomware, and adware.
- Social Engineering – A technique used by cybercriminals to deceive and manipulate individuals into providing sensitive information or undertaking actions that could harm themselves or their organization. Forms of social-engineered cyberthreats include phishing, spear phishing, smishing, baiting, and pretexting to name just a few.
- Man-in-the-Middle (MitM) Attacks – A cyberattack in which the attacker intercepts the communication between two parties with the aim of eavesdropping, stealing information, or altering the conversation. By positioning themselves between the sender and receiver, the attacker makes it seem as if the two parties are communicating directly with each other but, in reality, all messages pass through the attacker.
Risk Mitigation
Cybersecurity threats are ubiquitous, very real, and occur frequently. Individuals and local governments should consider:
- Establishing procedures to detect and prioritize cybersecurity threats;
- Connecting risk-mitigation strategies to the local government’s goals and enterprise risk management, and
- Encouraging both decentralized accountability and robust decision-making processes. It’s on everyone to say something if they see something.
Other helpful practices include software updates and patching, security protocol implementation, and disaster recovery planning; experts agree that employees throughout the organization are key. Providing regular training and testing employees on cybersecurity best practices like recognizing and reporting phishing and related social engineering campaigns; using strong passwords; locking desktops when unattended; and identifying suspicious activity can help mitigate the risk of successful cyberattacks. Human error, whether unintentional or deliberate, and insufficient cyber-risk education are among cybersecurity’s weakest links and, therefore, easiest to exploit.
What’s Next for Your Local Government?
At COLOTRUST, we prioritize cybersecurity and have taken measures to help reduce the risk of cyberattacks against our clients’ assets. We have implemented internal controls and advanced technology towards achieving this goal, and we reassess protocols, processes, and procedures on an ongoing basis. However, COLOTRUST is only one part of the client / advisory equation, and as such, cyberattacks targeting the systems maintained and overseen by the local governments we serve are often beyond our firm’s technology and controls.
Given the rising severity and scope of cyberthreats targeting local government entities, we strongly advise our local government clients and participants to assess their own system vulnerabilities and information security protocols to better protect themselves against the significant threat and impending loss that can accompany cyberattacks. It’s not enough to have crown jewels in the vault if the door is unlocked. Although COLOTRUST can’t be your ‘personal locksmith,’ we want to share what we have learned about cybersecurity with you; while no local government is completely secure nor able to totally shut out all nefarious behavior, by implementing available cybersecurity risk-mitigation strategies, local governments can help reduce the risk of a successful cyberattack and better protect themselves.
Click below to download the newest whitepaper Cybersecurity Best Practices: Protecting Your Local Government and What Matters Most authored by the Chief Information Officer at Public Trust Advisors, LLC (COLOTRUST Administrator and Investment Advisor) to learn more about best practices your local government can begin using today to assist in protecting your community! Download our whitepaper today and learn more about cybersecurity for your local government.
Cybersecurity Best Practices Whitepaper Download
Written By:

Brian Sugrue
Chief Information Officer
Public Trust Advisors, LLC

